DepEd CAR Database Leak Exposes Over 6 Million Records, Including 30,000+ Teacher Personal Information
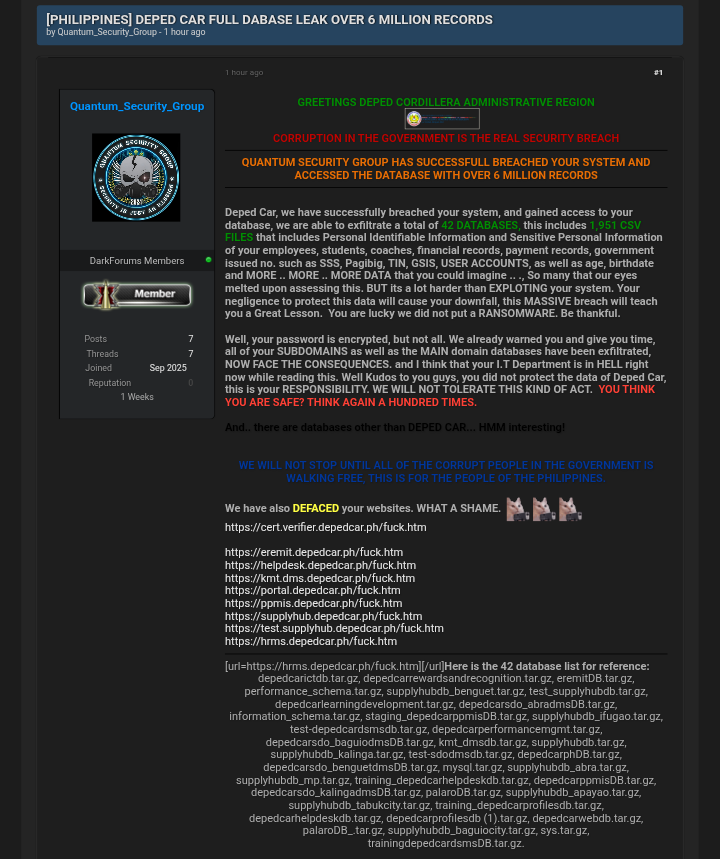
A massive data breach has struck the Department of Education – Cordillera Administrative Region (DepEd CAR), after a hacking group calling themselves Quantum Security Group claimed responsibility for successfully compromising internal systems and exfiltrating over six million records across 42 databases.
Screenshots posted in underground forums reveal that the attackers gained full access to the database trainingdepedcardmsDB and other systems hosted under the DepEd CAR domain. The leaked Adminer SQL management panel shows tables containing hundreds of thousands of entries, such as those recording document tracking, internal memos, attachments, user tags, and official communications. For example, the document_track and document_track_dest_division tables alone contain nearly 200,000 records each, while the document table holds close to 26,000 entries. Attachments, memos, and other sensitive operational data also appear to have been taken.
Upon reviewing the first batch of leaked files, the team confirmed the presence of more than 30,000 teacher records that go beyond basic personal identifiers. Each entry contains a full profile including employee ID, complete name, sex, and birth date, alongside demographic details such as ethnicity and educational attainment. These records also include work-related data such as office, division, section, and school assignments, as well as the teachers’ official position titles. Alarmingly, account information is also stored in the database: usernames, email addresses, and passwords, some of which appear to be in plaintext or weakly encrypted are linked to each user profile. Metadata such as account creation dates, last login attempts, and status fields (whether the account is active, permanent, or flagged for first-time login) further confirm that these are live, operational accounts connected to DepEd CAR’s systems. This means that not only personal information but also credentials that can be used for unauthorized access have now been exposed.
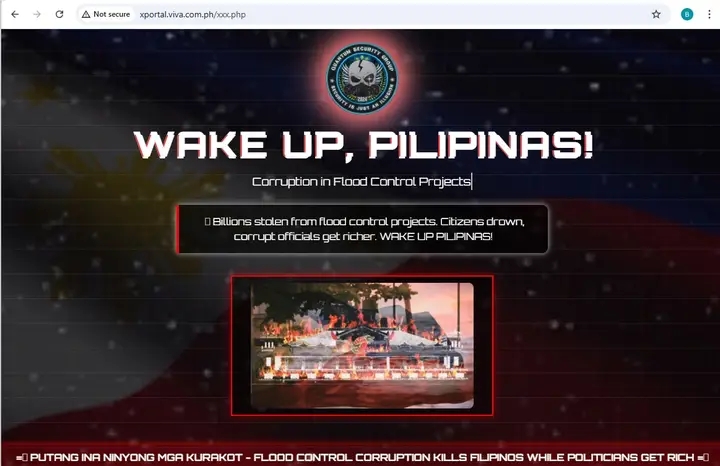
Beyond the data theft, the attackers also defaced several DepEd CAR subdomains. Visitors to affected sites, including the verification portal, helpdesk, supply hub, HRMS system, and even testing environments found altered pages with derogatory messages and the suffix “/fuck.htm” added to URLs. The simultaneous defacement of multiple domains is strong evidence that the attackers maintained deep access across the organization’s infrastructure, not merely a single entry point.
In their announcement, Quantum Security Group justified the attack by pointing to alleged corruption and negligence within government systems. Their message declared that while many of the stolen passwords were encrypted, others were not, and they emphasized that the breach was intended to serve as a “lesson” rather than a ransomware attack. The group warned that this incident should be taken as a wake-up call, writing: “You did not protect the data of DepEd CAR, this is your responsibility. You think you are safe? Think again a hundred times.” They also suggested that databases from other DepEd regions may already be in their possession.