Essential Dos and Don’ts for Using the Tor Browser
By: Elizze F. Serna | Editor in Chief
Over the past seven years, I’ve explored the hidden layers of the internet—the “dark web”—where anonymity, freedom, and danger often coexist. What started as curiosity eventually became a calling. I didn’t just learn how to use the Tor Browser—I learned how to survive the dark corners of the web, spot scams, detect social engineering patterns, and stay safe in an environment that constantly evolves.
In that time, I also saw the real-world consequences of poor digital hygiene: exposed credentials, stolen identities, and even entire companies brought down by a single leak. And I realized: exploring the dark web isn’t just about accessing .onion sites—it’s about understanding the fragile state of our digital privacy.
That's part of why I became involved with Deep Web Konek, a cybersecurity advocacy group focused on monitoring breaches, exposing fake services, and helping ordinary Filipinos understand how to protect themselves in a world where their data is constantly at risk. We’ve tracked thousands of leaked credentials, including phone numbers, government IDs, and sensitive corporate data. And many of those leaks—yes—were floating around on dark web forums that most people don’t even know exist.
So when someone asks me for tips on using the Tor Browser, I don’t just give a checklist. I tell them what I’ve learned the hard way.
✅ DOs: What You Should Do When Using the Tor Browser
1. Use only the official Tor Browser.
Download it directly from the Tor Project website. Anything else, especially apps from unofficial app stores or websites, is a security risk.
2. Prefer .onion services whenever available.
Onion services offer end-to-end encryption within the Tor network. Many clearnet websites (e.g., ProPublica, DuckDuckGo) offer .onion mirrors for better anonymity.
3. Use strong, unique credentials.
Don’t reuse emails, usernames, or passwords you use in real life. If one of your accounts gets compromised, reused credentials are often the first breadcrumb used to trace you. A password manager like KeePass (offline) helps here.
4. Keep Tor Browser updated.
Outdated versions can contain known vulnerabilities. Make it a habit to check for updates regularly—your privacy depends on it.
5. Use bridges or pluggable transports if Tor is blocked.
If you're in a country or network that blocks Tor, use Tor bridges or obfs4 pluggable transports to bypass censorship and continue using Tor safely.
6. Use Tails or Whonix for higher anonymity.
For activities that require extreme anonymity, consider using live operating systems like Tails or Whonix, which are specifically designed to route all traffic through Tor.
7. Understand your threat model.
Tor helps with network anonymity, but it doesn't protect against all types of surveillance, malware, or user error. Know what you're up against and adjust accordingly.
❌ DON’Ts: What You Should Avoid at All Costs
1. Don’t install browser plugins or add-ons.
They can leak your real IP address. Even privacy tools can backfire if they aren’t designed to work with Tor.
2. Don’t torrent over Tor.
BitTorrent leaks your real IP even when configured to go through Tor. Plus, it slows the network down for everyone.
3. Don’t use unofficial Tor browsers.
Apps like “Onion Search Browser” often contain ads, tracking scripts, or worse. They offer a false sense of security.
4. Don’t enable JavaScript or site features carelessly.
JavaScript can be used to fingerprint users. Use Tor’s “Safest” setting when visiting sensitive sites, which disables most risky features.
5. Don’t trust every .onion site.
Just because a site is on the dark web doesn’t mean it’s legit. Many are phishing scams, clones, or outright malware delivery vehicles—especially finance-related ones.
6. Don’t use personal accounts or real info.
Logging into your real email, bank, or social media accounts via Tor connects your real identity to your Tor traffic. Use separate aliases.
7. Don’t use Tor + VPN blindly.
Using a VPN before Tor (VPN → Tor) hides Tor usage from your ISP, but you're now trusting your VPN provider. VPN companies can be compromised, or worse, malicious. Tor bridges are safer alternatives for avoiding detection.
8. Don’t assume you’re invisible.
Tor improves anonymity, but it doesn't make you invincible. Mistakes, downloads, or even simple behavior patterns can still expose you.
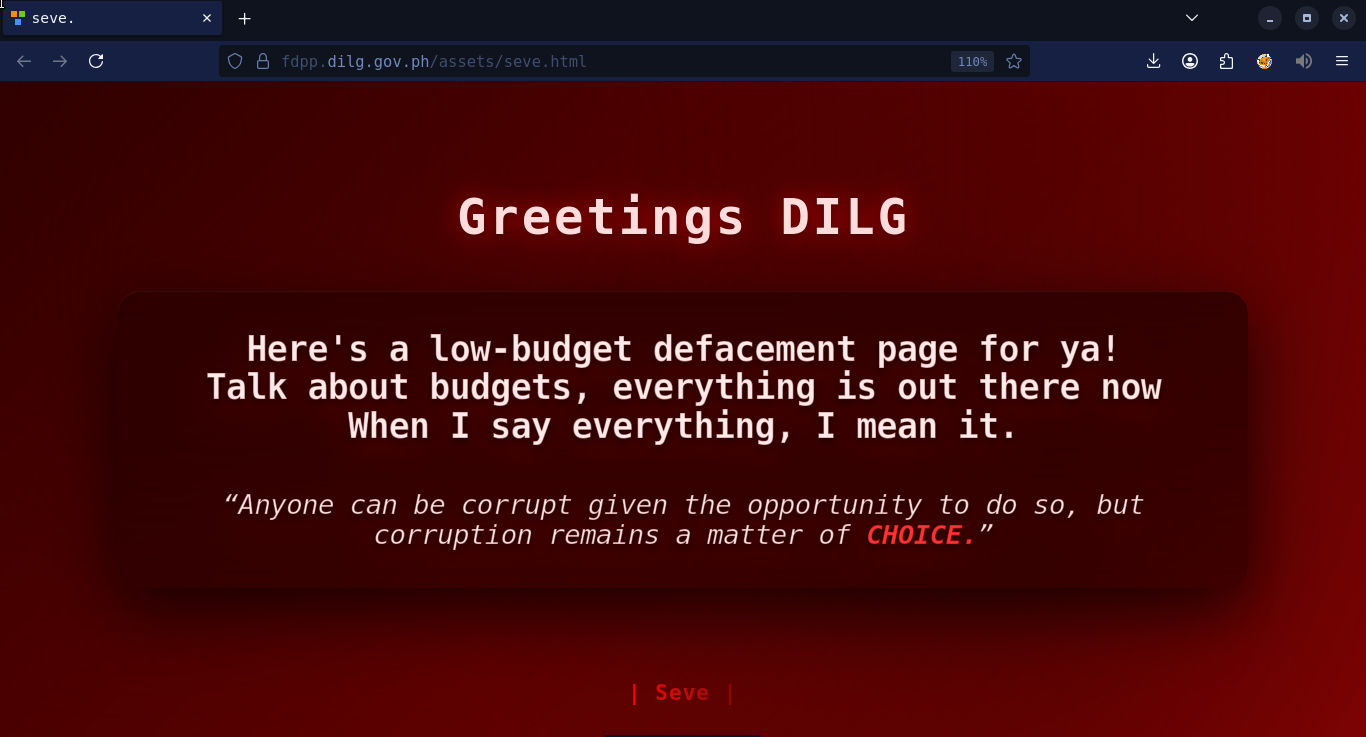
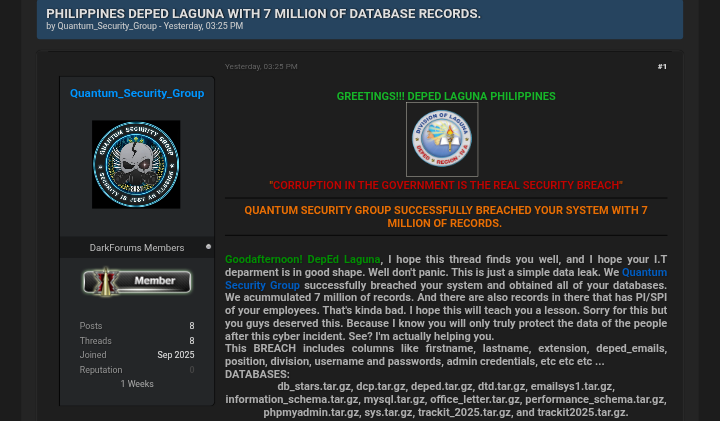
Here in the Philippines, data breaches have become alarmingly common. From government agencies to private companies, we've seen millions of records—many containing phone numbers, emails, passwords, and even passport data—end up on dark web marketplaces.
At Deep Web Konek, we’ve identified and tracked breaches affecting all sectors. In many cases, we’ve found stolen data being advertised on Tor-only forums or dark net marketplaces mere hours after an attack.
Through our various initiative, we notify victims, analyze breach origins, and even engage with telcos, hosting providers, and authorities to reduce exposure and raise public awareness.
We also run educational campaigns simulating “leak searches” and demonstrating how a few pieces of leaked data can lead to identity theft, SIM swaps, and financial fraud. Tor is a part of that conversation—not because it’s evil, but because it’s where many attackers operate.
Using Tor isn’t just about curiosity anymore—it’s about control. It’s about reclaiming your digital identity in a time where data breaches are no longer rare events, but weekly headlines.
Tor Browser is a tool. Used correctly, it empowers whistleblowers, journalists, researchers, and everyday people in hostile environments. Used carelessly, it’s a liability.
So ask yourself:
1. Are you using Tor to explore?
2. To protect your identity?
3. Or simply to see what’s out there?
Whatever your reason, use it wisely. Learn the basics, read the documentation, and never stop questioning what you see—even on the dark web.
Because out there in the shadows, what you don’t know can hurt you.